Using this entity in your queries retrieves results with an identified domain.
You can apply a full domain value (either a single one or in a series of up to 3 words), a partial one or a group of domains to this filter.
Identify a masked domain
It is important to mention that this entity identifies valid links (e.g. https://linkedin.com), masked domains (e.g. linkedin[.]com), and domain mentions that are not links (e.g. linkedin.com).
Note: The domain entity detects and is valid only for documents crawled from November 1, 2020.
Here are a few ways you can use this filter:
Monitoring mentions of company domains in the dark web
The mentions of company domains in the dark web can alert a company to possible threats just as mentions of the name of the company or its products do. Since the company domain is one of the most visible identifiers of a company, hackers often use it to refer to a company.
The following query retrieves different results in which the company domain was detected. This query detects different forms of the queried domain (i.e. not limited to a valid domain structure) in the context of data breaches. By adding keywords related to a specific or general cyber threat, we can monitor mentions of the company domain that indicate a possible data breach.
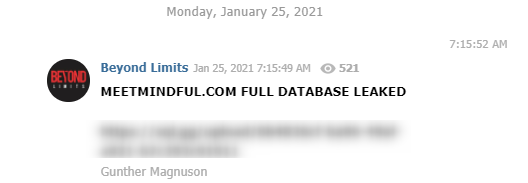
Query: *enriched.domain.value:(meetmindful.com) AND (leak OR accs OR database OR account OR login OR logs OR "mail pass")
- Here is an example of a database leak of MeetMindful.com that was shared in a Telegram channel:
These types of queries allow the user to separate mentions of the company name and mentions of the domain. This is particularly useful as domains are a common target for cyberattacks. Company names, on the other hand, are often mentioned in the context of other scams, frauds, and illegal activity.
Tips:
- When querying mentions that only contain the company name (and exclude the domains in the same query), remember the results don’t necessarily include risks to the domain.
(For example, in the query above, a query mentioning the company name that excludes its domain receives twice as many results.) - It is recommended to include terms related to threats (hacking, financial fraud and others) in the query, as shown in the example above. The domain entity identifies documents containing links and mentions of the queried domain that include those terms. This reduces the amount of irrelevant content (such as shared links as a part of a discussion) and retrieves results that mentions domains in the context of a risk.
- For the most comprehensive coverage, it is recommended to combine the domain entity with other company identifiers (such as the company name) and terms that describe different kinds of threats.
Monitoring links for the purpose of discovery
Another common use case for links is the monitoring of sources mentioned by other actors in the dark web. For example, you can find posts from hackers on Telegram channels with links about specific topics, the latest marketplaces in TOR networks discussed by buyers and hackers, and more.
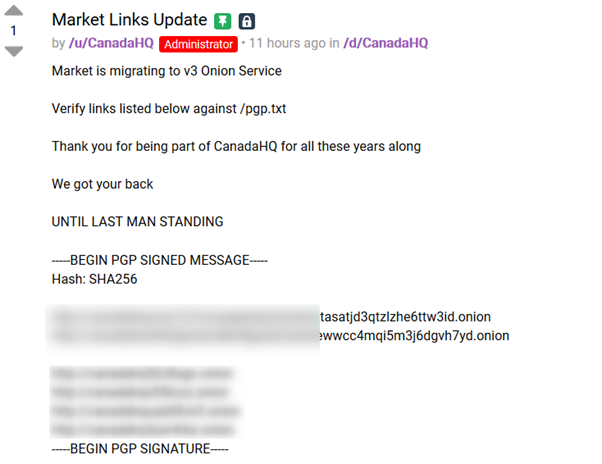
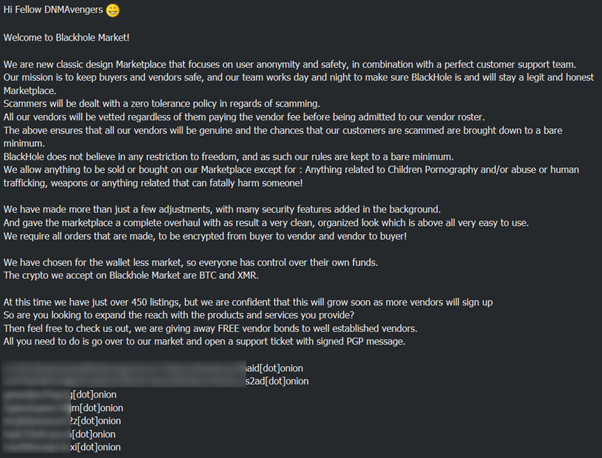
The following query will retrieve results with onion links from different forums in the TOR network, specifically marketplace links.
Query: (site.type:discussions AND extended.network:tor) AND enriched.domain.value:.onion AND (market OR marketplace)*
The following posts are an example of new marketplace links shared online.
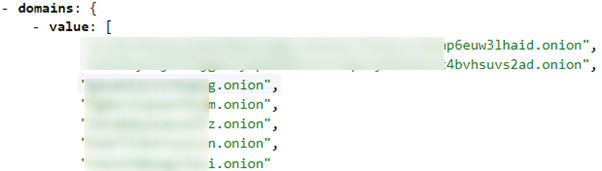
This is how it looks in the Cyber API output.
Although the mentioned domains are masked with a [dot] instead of a . between the suffix and the domain, we can still detect them as domain entities.
We explain this more in the next section.
Monitoring censored (“hidden”) domains (e.g ones that hackers or actors are masking)
To avoid automated detection of links, many hackers and actors in the dark web often mask links they mention. As shown in the example above, one of the ways to do that is with a [dot] that replaces the actual dot in the domain. Other ways are spaces, parentheses and brackets which break the proper link.
The example above shows the detection of a common permutation of domains in the dark web. The domain filter expands the coverage of mentioned domains more than a single query does using the extended.external_links filter or as free text.
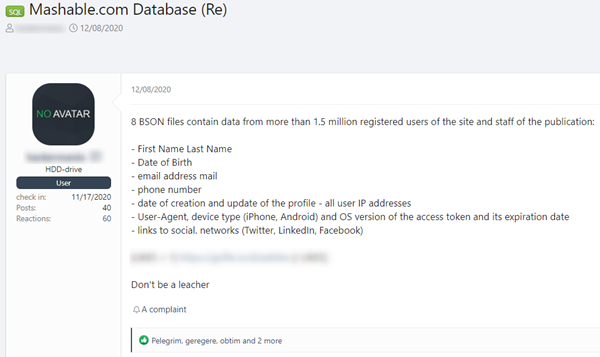
Another great example is the one below, where a hacker posts a database of the website Mashable.com, an American culture and technology news website, in a known hacking forum. A Mashable data breach was reported in November 2020.
Query: (database) AND enriched.domain.value:Mashable.com AND -site.domain:pastebin.com
Note that the website’s domain is not a valid link, and could not have been detected by the extended.external_links filter.